Andrew McCarthy asked a good question last Thursday: why hasn’t Trump publicized results of the investigation of the unmasking of his campaign/ transition teams by Obama officials? As McCarthy points out that Trump has the ultimate authority to do just that:
I’ve watched the story closely but I haven’t written about it for a while because I can’t get past a nagging question: Why must we speculate about whether the Obama administration abusively exploited its foreign-intelligence-collection powers in order to spy on Donald Trump’s political campaign? After all, Trump is president now. If he was victimized, he’s in a position to tell us all about it.The president is in charge of the executive branch, including its intelligence agencies. He has the authority to decide what intelligence information, and intelligence abuses, can be declassified and made public.
Because Trump hasn’t done this, when surely he would be motivated to, McCarthy feels compelled to at least consider the possibility that the “unmaskings” probe may be a way for Republicans to dangle Democrats, just as the “Russia” theme is a way for Democrats to dangle Trump.
The poisonous thing about the Trump-Russia “collusion” controversy is that it appears to be more a political narrative than a real collaboration in serious malfeasance, notwithstanding the president’s penchant for acting like a guilty man. Is “political spying,” similarly, a narrative — just from the other side? At a certain point, don’t we have to wonder whether the people with access to the relevant information have decided they are better served by innuendo than disclosure?
This is an excellent question, not because I think the Republicans in Congress are just playing games, but because the question itself highlights something the public has never really understood.
McCarthy writes as if unmasking the unmaskers is a simple matter of digging out the records of unmasking requests. But the act of “unmasking” hasn’t looked like that, procedurally, for a number of years now.
If Susan Rice – a very high-level executive – tasks her subordinates to bring her unmasked data on Trump associates, she may leave a readily-auditable procedural trail of what happened.
But Susan Rice didn’t perform the key actions involved in abstracting the identities of U.S. persons from the raw database information.
Her subordinates did – whether they literally did it themselves (and some of them no doubt had that capability), or asked analysts in other agencies to do it.
It’s the nature of the procedure that needs to be better understood here. Americans have an overly formal idea of what happens today in an “unmasking.” That’s largely because the persons of interest in the House Intelligence Committee’s unmasking probe so far have been very high-level officials: Susan Rice, John Brennan, Samantha Power. It’s also because news reporters and even some of those in Congress have an outdated understanding of the mechanics of it.
Officials at very high levels, like Rice or Brennan, would make requests in some form that could result in intra- or interoffice procedural records. The officials themselves may literally have the ability to retrieve unmasked data on U.S. persons using searches on their own desktop computers. But they don’t have the time, and it’s not their job, and they probably never learned how to do it. They’re nosebleed-level executives. They don’t do keyboard cowboying.
The vast majority of actual unmasking occurs today on the informal model of keyboard cowboying. In a procedural sense, it’s limited by rules: the rules of FISA, its amendments, Executive Order 12333. In a functional sense, it is now limited by user permissions on the IT system.
The IT transformation of the intelligence community
The short version is that, if you as an employee with a clearance have access to unminimized (“unmasked”) data on U.S. persons – if you’re authorized to see it, should it be disseminated in a report from an intelligence agency – then in some if not all cases, your user permissions on the intelligence community network allow you to see it in the raw NSA database. (The links below make this clear.)
Additional user controls may apply if you’re going to search for and retrieve unminimized data (perform an “unmasking” action), as opposed to just viewing it after someone else has done that. Explicit information on that isn’t publicly available, but controls of this kind are probable, given the regulatory constraints on handling and dissemination of unmasked data. Such controls would go with your job (e.g., do you work at a certain level for an unmasking authority, like Susan Rice?). The practical effectiveness of these controls, over relatively short periods of time, would depend largely on your honesty as a user.
The original form in which the data exists is raw and unminimized. NSA has had such data for many years now, since the dawn of the era of digital records. (The size of the database ramped up considerably when the “war on drugs” was inaugurated during the Bush 41 administration. With the Internet revolution in the 1990s, it exploded exponentially.)
The raw information sits in the gargantuan NSA database waiting to be retrieved for national security purposes. If you have the ability to retrieve data from the NSA database, and your user permissions allow you to see unminimized data, you – the analyst sitting at your computer – can view it. (See former DNI James Clapper’s explicit vision for this, recounted in an industry-press discussion of a 2013 policy memo.)
In a stovepiped, less widely distributed form, this capability has been available outside NSA– namely, for CIA and FBI users – since 2002. It expanded to the National Counterterrorism Center (NCTC) in 2012. Early on, accessing the capability was an old-school matter of having special computer terminals.
But in the years since about 2011, the capability has been eased and broadly integrated into a community-wide IT network serving all 17 agencies of the IC: the Intelligence Community Information Technology Enterprise, or ICITE. During the years when Obama officials on the National Security Council and ODNI staffs may have been retrieving surveillance data on Trump associates (2015-2017), they had ICITE desktop clients on which to make such retrievals.
(Most if not all of them were probably “CIA users,” regardless of where their offices were. Some people involved in unmasking Trump associates may have been at DOJ or the FBI, which were also integrated with ICITE at that point. It is less likely that any “NSA users” were involved – but NSA’s network is also part of ICITE.)
Retrieving the data isn’t a simple matter of doing a search on “Donald Trump,” of course. If there’s no judge’s warrant to run that search, it wouldn’t be legal under the applicable statutes and regulations. In fact, reporting from the IT-industry media suggests that the user interface applications would balk if you tried that. There are some built-in safeguards to prevent users from running illegal searches on the NSA database.
Rather, a user without a warrant in hand is supposed to have a “foreign intelligence” purpose for running searches. In that context, analysts can search on the names and other identifying characteristics of foreign targets. To narrow searches down, the analyst can use specific metadata search terms relevant to the type of communication being searched on (e.g., email, text, some phone call records authorized for retention in the database. See the ODNI transparency report below for a flavor of such search terms).
If what a user is really looking for is raw data on U.S. persons (but without seeking formal authority), he or she needs to tailor searches in such a way that they will yield that data – without raising flags in the system by searching overtly for a red-flag term such as a U.S. person’s name.
Note the time factor here: the proliferation of ICITE clients was marked from 2014, when there were 9,000 users, to mid-2016, when there were 50,000. It was in the same period that the viewing of metadata relating to U.S. persons soared dramatically, according to an ODNI “transparency report” from April 2017. (Metadata is “non-content” information, but it is readily correlatable to an individual U.S. person.)
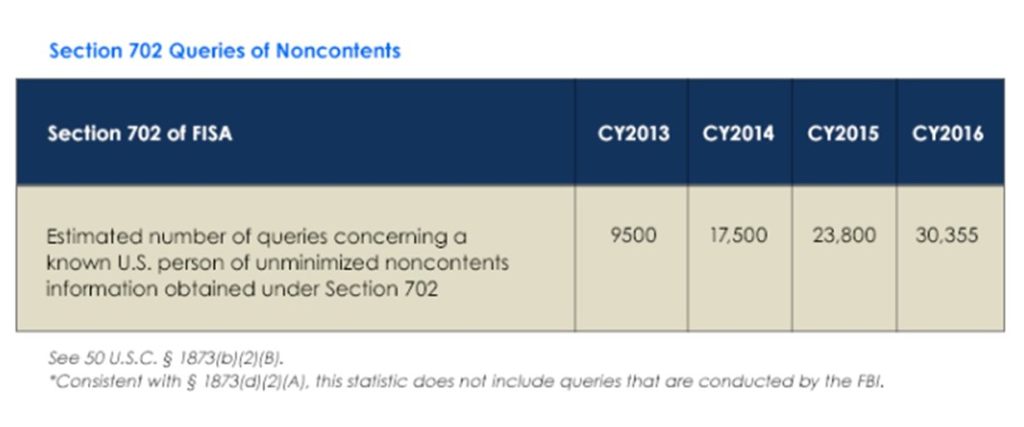
Regarding search terms for unminimized U.S. person data, ODNI reports only the figures for 2015 and 2016. There was a 13% increase from 2015 to 2016. This may not seem like much; however, metadata searches – which increased at a dramatic pace over the same period – would enable analysts to accomplish more-targeted unmasking searches with fewer search terms.

Overall, the increase in both categories of search was significant, coincident with the expansion of ICITE and the ability of analysts to run direct queries from their desktops on a common network.
Understanding this leads to a more accurate view of what it takes to determine who has been unmasking U.S. person identifying (USPI) information.
The IT revolution transformed the essential nature of unmasking
It’s not a matter of looking for formal records somewhere, in a designated place where those records are supposed to be. In fact, we can be pretty confident that’s not even how the initial discovery about Susan Rice came about.
Rice probably wasn’t making “formal” unmasking requests that were recorded in a prescribed “unmasking log” somewhere. Rather, she was issuing intraoffice tasking to have data retrieved and organized for her perusal. We only know about it today because a Trump-hired official on the NSC staff found evidence of the tasking, sometime between the end of January and mid-March 2017.
(If there were some formal log of the tasking to unmask Trump associates, as Andrew McCarthy seems to envision, it would – as he says – have been extremely easy to gather the information months ago.)
Moreover, it is virtually certain that many of the various actions that qualify as unmasking were not being prompted by prior formal reporting from NSA. This is a key point and one that many commentators don’t understand.
NSA has reporting priorities set by national security priorities and makes formal reports on only a small percentage of what it vacuums in 365 days a year. NSA’s reports are on foreign intelligence topics.
But analysts outside NSA are less and less reliant today on formal reports for their cueing.
The ability of outside analysts to retrieve data from NSA, even when no formal report has been made to cue them to its existence, is a core feature of the “Big Data” revolution, in which data collection is constant, and retrieval is episodic. The Big Data construct, with its key component of data mining, has in some ways reduced the operational significance of formal reporting by all intelligence agencies, including NSA.
The SIGINT expertise of NSA analysts will always be needed, of course, and their reporting will remain indispensable for a number of purposes. But merely alerting IC analysts to the existence of new information isn’t necessarily one of them anymore.
NSA has been committed throughout the “ICITE-ization” of the intelligence info-universe to making its raw database “discoverable.”
This has meant, in procedural terms, that the clear lines that once existed between collecting and holding raw data and making it available to outside users through refined “reports,” have been not just blurred but virtually erased.
That has profound implications. It means that applying the rules of FISA and E.O. 12333 has become increasingly a matter of interpretation under new conditions. “Dissemination” and “reporting” take on a different meaning, when an analyst outside NSA can literally view raw, unminimized data without having to ask NSA for it via a specially-responsive “report.” (See here for a relevant, top-level discussion of the info-ownership implications of modern data-sharing capabilities.)
Was a “report” created when a spreadsheet was made for Susan Rice? Did it constitute “dissemination” of unminimized data if an intel agency representative on the NSC staff retrieved it for her?
There was a time – 15 years ago – when there were cut-and-dried answers to the analogous questions of that earlier time. But “unmasking” isn’t essentially about formally-disseminated “reports” anymore. There’s not necessarily a time-stamp on when data became “known” to community users now or a formal record of who would have seen it.
Rather, the most accurate way to determine how much unmasking is going on is to look at the system logs of computer transactions, and see how search terms have been used, what cells of data were “touched” by a search (if that can be determined), and which users were systematically making searches that may have resulted in questionable unmaskings.
That in itself is not as easy as it may sound. This new reality should help clarify why the House’s unmasking probe isn’t a simple matter of looking for discrete actions by officials that qualify in a formal sense as unmasking. If there was never a formal report issued containing unminimized data on USPI, it takes some Olympic-level IT forensics to figure out (a) that someone was trying to ferret out specific USPI (e.g., on Trump associates), and (b) who was doing it, and – if possible – what they did with the data.
Enter the cloud
A final piece of the IT puzzle is the adoption of IT cloud technology by the intel community in the period 2010 to 2016. NSA migrated its colossal raw SIGINT database to an NSA-operated cloud in 2013 (IC GovCloud; see links above), and now functions within ICITE as a cloud-services provider for the 16 other IC agencies.
But there is a second cloud in ICITE: the CIA-contracted Commercial Cloud Services (C2S) cloud operated for the IC by Jeff Bezos’ Amazon Web Services, out of a facility in Northern Virginia. C2S rolled out from 2014 to 2016, also serves all 17 IC agencies. The existence of both clouds – which are eventually to be migrated to a more integrated operating mode – complicates the forensic problem for an unmasking probe.
The actual retrieval of NSA data presumably takes place via NSA-hosted applications. (See Ars Technica on ICREACH, above. NSA pioneered the IC’s first cloud and “app mall,” and we can assume that in ICITE, the main analyst service provided by NSA – processing SIGINT – is still brokered through NSA-originated systems.)
But once an analyst has retrieved the data, its use and further dissemination in applications operated in the C2S cloud cannot be excluded. In fact, the key to whether an unmasking-data retrieval was improper may well lie in what was done with it outside of the NSA-auditable IT network. The records could be in the system logs of the C2S cloud.
Or there could be no additional IT records at all – if a user just retrieved the data and then wrote it down on a sheet of paper.
As regards the auditability of the ICITE clouds, federal regulations provide for built-in capabilities. An IT security standard called Federal Risk and Authorization Management Program – FedRAMP – was developed to make sure that cloud transactions could be tracked, identified, and audited, and that some transactions would create security alerts for administrators. (See here as well.)
But with a man in the loop between one cloud and another, it’s conceivable for data to lose its inherent security tagging – e.g., in the NSA cloud – if it is manually entered for sharing or analytical purposes in the C2S cloud.
How well is the audit capability working?
Short answer: we don’t really know. That is visible in the ODNI transparency report from April 2017, first because NSA, CIA, and FBI don’t necessarily track and record their acknowledged unmasking actions the same way.
As seen above, NSA had to provide estimates of how many tens of thousands of relevant search terms have been used, in part because of these non-uniform agency practices.
But that uncertainty is compounded by the fact that, to a meaningful extent, NSA was discerning what was an unmasking action by interpreting the nature of searches. That doesn’t seem to be a perfectly exact science.
Following a 2016 report on FISA compliance, NSA was burned by a Foreign Intelligence Surveillance Court (FISC) judge when it confessed that a meaningful percentage of its data retrievals (about 5%) had violated the regulations on unmasking, through what NSA deemed to be mostly inadvertent use of faulty search terms. In most cases the search terms were left, reportedly by sloppy analysts, to include types of data that should have been excluded by more careful search tailoring.
NSA assessed that the violations were not willful. But the key point for our purposes here is that, in at least some cases, they would have looked the same to the system audit whether they were willful or not.
NSA vowed to close the identified vulnerabilities down, and some progress was apparently made.
But the FISC judge was appalled, and watchdog groups have not been reassured by improvements made since the problem was first identified (as early as 2013). In April 2017, NSA decided to suspend a particular type of data retrieval (the so-called “about” data queries of “upstream” data collected under FISA Section 702), which was especially likely to produce violations. Notably, the type of data retrieval in question was directly relevant to unmasking Trump associates in 2015-2016. The judge, commenting here on the previously undisclosed frequency of those data queries, was referring in part to that time period.
“Since 2011, NSA’s minimization procedures have prohibited use of U.S.-person identifiers to query the results of upstream Internet collections under Section 702,” the unsealed court ruling declared. “The Oct. 26, 2016 notice informed the court that NSA analysts had been conducting such queries in violation of that prohibition, with much greater frequency than had been previously disclosed to the Court.”
Closing down the whole category of these queries is a positive step. But the overall level of estimative uncertainty in the ODNI transparency report from April 2017 shows that there remain reasons for concern.
The numbers themselves should concern us. Without better accountability for the whole process, the American people understandably won’t want to take it on faith that the intel agencies – wherever their users have their desks, including on the ODNI and NSC staffs – have had nothing but properly-scoped, legal searches of the NSA database going on.
Bottom line: at this point in 2017, the ability to accurately alert on, audit, and forensically interpret database searches that result in the targeted unmasking of U.S. person data is not necessarily an established, foolproof expertise.
Couple that with the problems of linking system-user activity to individual human beings, and determining what was done with the data after it was retrieved (a key to whether the unmasking was proper or not), and you have a much more challenging problem-set than many commentators imagine. It’s not surprising that, even four months after the revelation about unmaskings by Obama officials, we still don’t have a clear, incontrovertible accounting of who did what.
The big picture
Some uses of U.S. person data may be perfectly legal, even if we don’t like them. This point has been made a number of times already. But what is elided in that point is the gap between legality and propriety. The latter is a question for politics. The people get to decide when what may be legal is nevertheless unacceptable.
So, as Andrew McCarthy points out, the unmasking probe is not a law enforcement investigation. That is not its essential nature. It may or may not have involved crimes under the U.S. Code.
But it may still have involved actions by Obama officials that the people consider egregiously improper. The remedy may be legislative rather than judicial.
With the unmasking of U.S. person data by Obama officials, there are probably valid reasons why we don’t even know the extent of it yet. Moreover, the standard methods of prosecutorial investigation do not necessarily apply. For example, there may be deductive certainty from IT evidence that specific officials were involved. But if they can’t be charged with crimes, there’s no way to compel testimony from them, and figure out the whole enterprise by getting them to explain their motives or implicate others.
There is also the “extreme care” factor we must assume to be in play. The searchers for the truth don’t want to improperly accuse intel system users whose actions are being interpreted through a set of deductive filters.
We got lucky with the initial clue on Susan Rice – which also implicated John Brennan (as a recipient of the collated information Rice ordered up). That one was based on procedural evidence.
But the time it took to identify Samantha Power, and now Ben Rhodes, as persons of interest tells me that the probe is, in fact, being done through IT forensics – a tool-set we know is available, but one we have reason to believe is imperfect.
At this point, collating publicly available information about auditing our intelligence systems poses no danger to the House probe. The system logs needed for this approach have presumably been secured against tampering by now.
But if I were on the House Intelligence Committee or in the Trump White House, I don’t think I’d be ready to go definitively public with whatever findings there are. Not yet.
Cross-posted with Liberty Unyielding
http://lidblog.com/the-obama-unmasking/
http://www.thegatewaypundit.com/2017/08/weakness-obama-admin-refused-stop-russian-interference-retaliation-fears/
http://www.thegatewaypundit.com/2017/08/weakness-obama-admin-refused-stop-russian-interference-retaliation-fears/

No comments:
Post a Comment